Are you ready to take the next step in your career as an Information Security Officer? Crafting a standout CV is crucial in a competitive job market where employers seek candidates who not only possess technical skills but also demonstrate a strong understanding of security protocols and risk management. In this comprehensive guide, we will walk you through the essential elements of an impactful CV tailored specifically for Information Security Officers. By the end of this article, you'll understand how to effectively showcase your expertise and accomplishments, ensuring your application stands out. Here’s what you can expect to learn:
- Understanding the Role: Insights into the key responsibilities and skills required for an Information Security Officer.
- CV Structure: A breakdown of the ideal layout and sections to include in your CV.
- Tailoring Your CV: How to customize your CV for specific job applications and highlight relevant experiences.
- Keyword Optimization: Tips for incorporating industry-specific keywords to pass through applicant tracking systems (ATS).
- Achievements Over Duties: The importance of quantifying your successes and articulating your impact in previous roles.
- Professional Summary: Crafting a compelling summary that captures your professional journey and aspirations.
- CV Example: A real-life example of a CV for an Information Security Officer to guide your writing process.
Dive into this guide to transform your CV into a powerful tool that opens doors to exciting career opportunities!
What is a Information Security Officer CV?
A well-crafted CV for an Information Security Officer plays a crucial role in showcasing an individual's expertise and experience in safeguarding organizational data and infrastructure. This document serves as a professional summary that highlights relevant qualifications, certifications, and technical skills necessary for protecting sensitive information from cyber threats. An effective CV not only outlines past roles and responsibilities but also demonstrates the applicant's ability to implement security measures, conduct risk assessments, and respond to incidents. For those looking to create a standout CV, following a comprehensive cv writing guide can provide valuable insights into structuring and presenting information effectively.
The importance of a CV for an Information Security Officer extends beyond job applications; it reflects the candidate's understanding of security protocols and their commitment to ongoing professional development in a constantly evolving field. A well-organized CV can significantly enhance the chances of landing an interview, as it allows potential employers to quickly assess qualifications and experience. Utilizing a cv maker can simplify the process of creating a polished and professional CV that aligns with industry standards, ensuring that the individual stands out in a competitive job market.
Key Components of a Information Security Officer CV
- Contact Information: Include your full name, phone number, email address, and LinkedIn profile link at the top of your CV.
- Professional Summary: A brief overview highlighting your experience, key skills, and what you bring to the role of Information Security Officer.
- Key Skills: Showcase your relevant abilities, such as risk management, incident response, and knowledge of security frameworks. For a detailed breakdown of essential skills, visit skills.
- Certifications: List any relevant certifications, such as CISSP, CISM, or CompTIA Security+, which demonstrate your expertise and commitment to the field.
- Work Experience: Detail your previous positions related to information security, including job titles, companies, and dates of employment. Emphasize specific achievements and responsibilities. More on structuring this section can be found at work experience.
- Education: Include your highest degree obtained, the institution’s name, and graduation year. Relevant coursework or honors can also be mentioned.
- Technical Skills: Highlight specific tools and technologies you are proficient in, such as firewalls, intrusion detection systems, and encryption methods.
- Projects: Describe significant projects you have worked on that showcase your information security capabilities, including any initiatives you led or contributed to.
- Professional Affiliations: Mention any memberships in organizations such as ISACA or (ISC)², which can add credibility to your profile.
- Publications and Presentations: If applicable, list any articles, whitepapers, or presentations you've authored or delivered related to information security.
- Awards and Recognition: Highlight any awards or accolades you've received in your professional career that pertain to information security.
- References: Optionally, include references or state that they are available upon request, ensuring to inform your references beforehand.
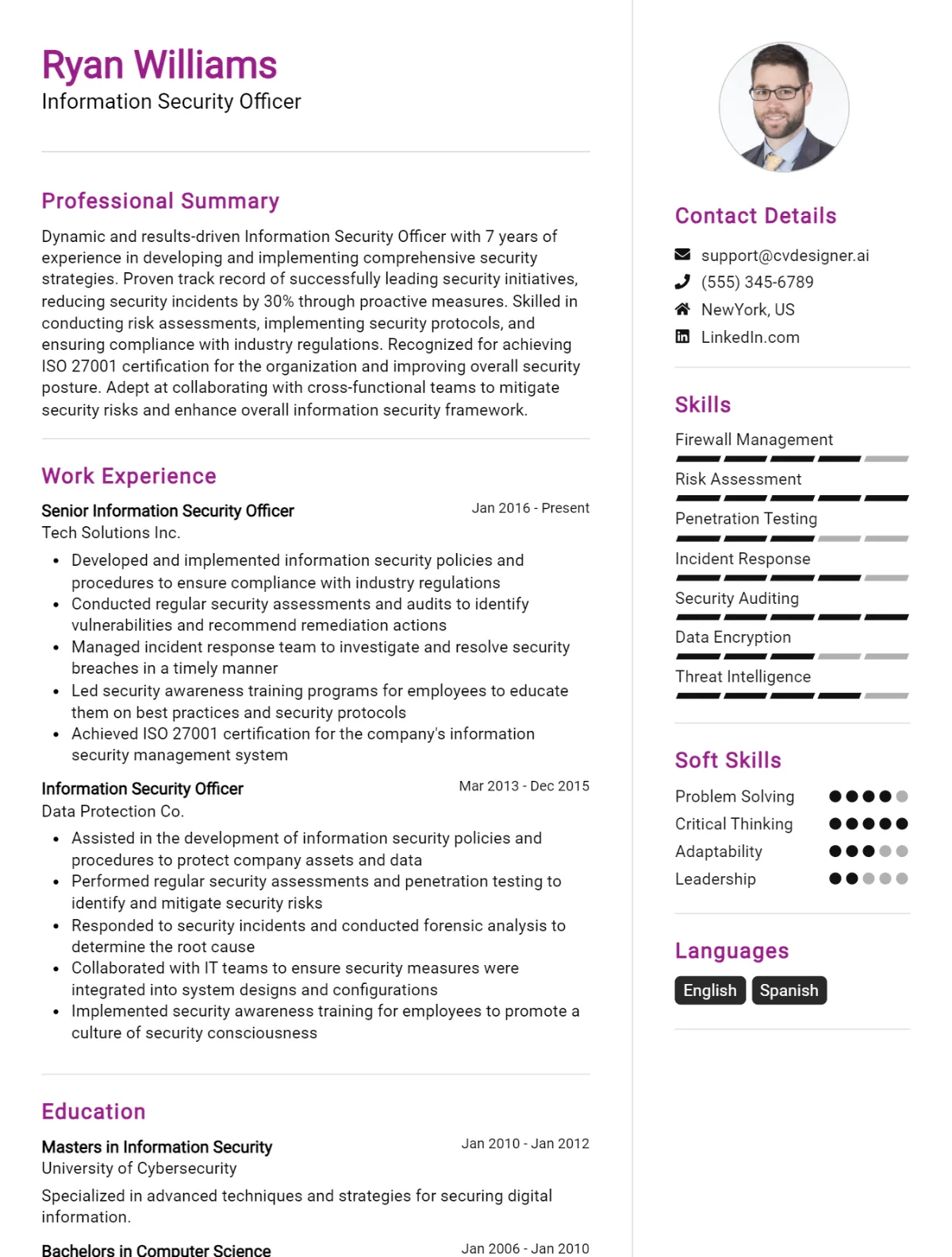
Sample Information Security Officer CV for Inspiration
[Your Name]
[Your Address]
[City, State, Zip Code]
[Your Phone Number]
[Your Email Address]
[LinkedIn Profile]
Professional Summary
Dedicated Information Security Officer with over 7 years of experience in implementing and managing comprehensive security programs to protect sensitive information and mitigate risks. Proven track record in developing security protocols, conducting vulnerability assessments, and leading incident response initiatives. Strong analytical and problem-solving skills combined with a deep understanding of regulatory compliance and data protection laws. Passionate about upholding the highest standards of cybersecurity and fostering a culture of security awareness.
Work Experience
Information Security Officer
ABC Corporation, City, State
[Month, Year] – Present
- Developed and implemented a comprehensive information security strategy that reduced security incidents by 40% over two years.
- Conducted risk assessments and vulnerability analyses, resulting in improved security measures and a 30% decrease in potential threats.
- Led incident response teams during security breaches, coordinating with IT and legal departments to mitigate damage and ensure compliance with regulations.
- Created and delivered security awareness training programs for employees, fostering a culture of security and improving compliance rates by 50%.
- Managed the implementation of security technologies, including firewalls, intrusion detection systems, and encryption protocols.
Information Security Analyst
XYZ Technologies, City, State
[Month, Year] – [Month, Year]
- Monitored security systems and responded to security incidents, ensuring timely resolution and minimal impact on business operations.
- Assisted in the development and documentation of security policies and procedures aligned with industry best practices and regulatory requirements.
- Conducted regular security audits and assessments, identifying areas for improvement and ensuring compliance with applicable laws.
- Collaborated with cross-functional teams to design and implement security measures for new projects and initiatives.
- Provided technical support for security-related issues, enhancing overall system security and user awareness.
IT Security Specialist
Tech Solutions Inc., City, State
[Month, Year] – [Month, Year]
- Supported the implementation of security solutions, including antivirus software, data loss prevention, and disaster recovery plans.
- Performed regular security assessments and penetration testing to identify vulnerabilities and recommend remediation strategies.
- Assisted in compliance audits, ensuring adherence to frameworks such as ISO 27001 and NIST standards.
- Maintained security documentation and reporting, contributing to continuous improvement of security practices.
Education
Bachelor of Science in Cybersecurity
University of Technology, City, State
[Month, Year]
Certifications
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- CompTIA Security+
- Certified Information Security Manager (CISM)
Skills
- Risk Assessment & Management
- Incident Response & Recovery
- Security Audits & Compliance
- Network Security & Firewalls
- Vulnerability Assessment Tools
- Security Information and Event Management (SIEM)
- Data Encryption & Protection
- Security Awareness Training
- Strong Analytical & Problem-Solving Skills
Publications
- "Enhancing Security Awareness in Organizations: Strategies and Best Practices," Journal of Cybersecurity, [Month, Year].
- "The Role of Information Security Officers in Modern Enterprises," Cybersecurity Review, [Month, Year].
References
Available upon request.
Information Security Officer CV Writing Tips
When crafting a CV for the position of an Information Security Officer, it’s essential to highlight your technical skills, relevant certifications, and experience in managing security protocols and policies. Begin with a strong personal statement that outlines your professional journey and key competencies in information security. Focus on quantifiable achievements and specific projects where you successfully implemented security measures or mitigated risks. Tailor your CV to match the job description, emphasizing your understanding of compliance standards, risk assessment, incident response, and security frameworks. Ensure your CV is well-organized, visually appealing, and free of errors to make a strong first impression.
- Tailor Your CV: Customize your CV for each application by incorporating relevant keywords from the job description.
- Highlight Technical Skills: Clearly list your technical competencies, such as familiarity with firewalls, VPNs, IDS/IPS, and encryption technologies.
- Showcase Certifications: Include any relevant certifications, such as CISSP, CISM, or CEH, as they demonstrate your commitment to the field and expertise.
- Quantify Achievements: Use metrics to showcase your impact, such as “Reduced security breaches by 30% through the implementation of new protocols.”
- Include Soft Skills: Mention soft skills like communication, problem-solving, and teamwork, which are crucial for collaborating with other departments.
- Professional Experience: Focus on your most recent roles and responsibilities, emphasizing your experience in risk management, compliance, and incident response.
- Education and Training: List your educational background and any specialized training that is relevant to information security.
- Keep it Concise: Aim for a CV length of 1-2 pages, ensuring that every section adds value to your application.
Information Security Officer CV Summary Examples
As an Information Security Officer, your CV summary should encapsulate your expertise in safeguarding sensitive information, implementing security protocols, and managing risk. It is essential to convey your experience, technical skills, and commitment to maintaining organizational integrity through effective security practices. Here are several examples of impactful CV summaries tailored for this role:
Dedicated Information Security Officer with over 8 years of experience in developing and implementing robust security policies and procedures. Proven track record in risk management, incident response, and compliance with industry regulations, ensuring the confidentiality and integrity of information assets.
Results-oriented Information Security Officer skilled in the latest cybersecurity technologies and frameworks. Expertise in threat assessment and vulnerability management, with a strong ability to lead cross-functional teams in mitigating risks and enhancing security postures across diverse environments.
Dynamic Information Security Officer with a comprehensive background in information risk management and security architecture. Adept in conducting security audits and vulnerability assessments, with a commitment to continuous improvement and training to foster a culture of security awareness within the organization.
Proactive Information Security Officer with a passion for defending information systems against emerging threats. Extensive experience in developing incident response strategies and conducting security awareness programs, resulting in significantly reduced security incidents and enhanced organizational resilience.
Experienced Information Security Officer with a strong foundation in both technical and managerial aspects of cybersecurity. Proven ability to align security strategies with business objectives, ensuring compliance with regulations while promoting a secure and efficient operational environment.
Build a Strong Experience Section for Your Information Security Officer CV
As an Information Security Officer, showcasing your experience effectively is crucial to demonstrate your expertise in safeguarding an organization's information assets. The following examples illustrate key responsibilities and achievements that can enhance your CV and highlight your contributions to previous employers.
- Developed and implemented a comprehensive information security strategy that reduced security incidents by 40% within the first year, ensuring compliance with industry standards such as ISO 27001 and NIST.
- Conducted regular risk assessments and vulnerability assessments to identify potential threats to organizational systems, leading to the implementation of corrective measures that improved the overall security posture by 30%.
- Managed incident response protocols, successfully leading a cross-functional team to mitigate a significant data breach, resulting in minimal downtime and protecting sensitive customer information.
- Spearheaded the deployment of a company-wide security awareness training program, increasing employee awareness of security best practices by 70% and significantly reducing the number of phishing incidents reported.
- Collaborated with IT and compliance teams to ensure that all security policies and procedures were up-to-date, resulting in a successful audit with no major findings and reinforcing the organization’s commitment to data protection.
- Designed and implemented a robust access control framework, utilizing role-based access control (RBAC) principles that enhanced data security and minimized unauthorized access risks.
- Established and maintained relationships with external security vendors and partners, negotiating contracts that saved the organization 20% in annual security expenditures while improving service quality.
- Led the investigation and analysis of security incidents, preparing detailed reports and presentations for senior management that informed strategic decisions and enhanced the organization's security governance.
Information Security Officer CV Education Examples
As an Information Security Officer, having a solid educational background is crucial for effectively managing and mitigating security risks within an organization. The following examples highlight relevant degrees and certifications that can enhance the qualifications of a candidate in this field:
- Bachelor's Degree in Cybersecurity: This program typically covers topics such as network security, ethical hacking, and risk management, providing a strong foundation in the principles of protecting information systems.
- Master's Degree in Information Security or Information Assurance: Advanced studies in these areas dive deeper into complex security challenges, policy creation, and strategic planning, equipping graduates with the skills necessary for leadership roles.
- Bachelor's Degree in Computer Science or Information Technology: A comprehensive understanding of programming, systems analysis, and database management can be beneficial for identifying vulnerabilities and implementing security measures.
- Certified Information Systems Security Professional (CISSP): This globally recognized certification demonstrates a deep understanding of information security concepts and best practices, making it a valuable asset for any Information Security Officer.
- Certified Ethical Hacker (CEH): This certification focuses on the techniques and tools used by malicious hackers, enabling security professionals to think like adversaries and better protect against potential threats.
Skills to Highlight in Your Information Security Officer CV
As an Information Security Officer, your role is critical in safeguarding an organization’s information assets against various threats and vulnerabilities. To effectively communicate your qualifications and capabilities in your CV, it is essential to highlight both your technical expertise and interpersonal abilities. Below are key soft and hard skills that are pertinent to this position.
Soft Skills:
- Analytical thinking
- Problem-solving
- Attention to detail
- Communication skills
- Team collaboration
- Risk assessment capabilities
- Adaptability to change
- Leadership qualities
- Ethical judgment
- Conflict resolution
Hard Skills:
- Knowledge of security protocols and standards (ISO 27001, NIST)
- Familiarity with firewalls, VPNs, and IDS/IPS systems
- Proficiency in cybersecurity tools (e.g., SIEM, DLP)
- Incident response and disaster recovery planning
- Understanding of network architecture and design
- Experience with vulnerability assessment and penetration testing
- Data encryption and cryptography knowledge
- Regulatory compliance expertise (GDPR, HIPAA)
- Security awareness training development
- Experience with risk management frameworks
Information Security Officer CV Format
As an Information Security Officer, crafting a well-structured CV is essential to showcase your skills and experience effectively. The best format for your CV may vary depending on your level of experience—entry-level, mid-level, or senior-level positions. Generally, a reverse-chronological format is recommended, as it highlights your most recent experiences first, making it easier for hiring managers to assess your qualifications quickly.
For entry-level positions, a functional format may also be beneficial, focusing on skills and relevant coursework rather than extensive professional experience. Mid-level candidates should opt for a combination format that emphasizes both skills and a chronological work history, while senior-level applicants should prioritize a comprehensive chronological format that details significant achievements and leadership roles.
- Entry-Level: Use a functional format that highlights relevant skills, education, and internships.
- Mid-Level: Choose a combination format to showcase skills alongside a rich work history.
- Senior-Level: Opt for a chronological format that emphasizes achievements, strategic initiatives, and leadership experience.
- Use bullet points: Clearly outline your responsibilities and accomplishments for each role to enhance readability.
- Tailor your CV: Customize your CV for each application, focusing on the specific requirements of the job description.
- Include certifications: Highlight relevant certifications, such as CISSP or CISM, to demonstrate your commitment to the field.
For more detailed guidance on creating an impactful CV, check out our cv format resource.
Common Mistakes to Avoid in a Information Security Officer CV
Crafting a compelling CV for the role of an Information Security Officer is crucial in a competitive job market. Since this position requires a blend of technical expertise, leadership skills, and a keen understanding of compliance and risk management, it's essential to present your qualifications effectively. To help you stand out, here are some common mistakes to avoid when creating your CV for this critical role:
- Neglecting to Tailor Your CV: Using a generic CV without tailoring it to the specific job description can lead to missed opportunities.
- Lack of Quantifiable Achievements: Failing to include measurable outcomes or achievements can make your contributions seem vague and less impactful.
- Ignoring Relevant Certifications: Not highlighting relevant certifications (like CISSP, CISM, or CEH) can diminish your credibility in the field.
- Overloading with Technical Jargon: Using too much technical language without providing context may alienate non-technical hiring managers.
- Inconsistent Formatting: A CV with inconsistent fonts, sizes, and layout can appear unprofessional and difficult to read.
- Omitting Soft Skills: Focusing solely on technical skills while ignoring soft skills, such as communication and leadership, can give a skewed impression of your capabilities.
- Excessive Length: A CV that exceeds two pages may overwhelm recruiters; aim for clarity and conciseness.
- Failing to Highlight Incident Response Experience: Not emphasizing your experience in incident response and threat management can be a significant oversight.
- Not Including Continuous Learning: Failing to mention ongoing education or training in the ever-evolving field of information security may suggest stagnation in your professional growth.
- Neglecting to Proofread: Spelling and grammatical errors can undermine your professionalism and attention to detail, which are critical in information security roles.
Key Takeaways for a Information Security Officer CV
- Contact Information: Clearly list your name, phone number, email address, and LinkedIn profile at the top of your CV for easy access.
- Professional Summary: Craft a concise summary that highlights your expertise in information security, key achievements, and career goals tailored to the specific role you’re applying for.
- Core Competencies: Include a section that features your key skills such as risk management, incident response, compliance, vulnerability assessment, and security architecture.
- Certifications: List relevant certifications such as CISSP, CISM, CEH, or other industry-recognized credentials that demonstrate your qualifications and commitment to the field.
- Work Experience: Detail your previous roles, focusing on responsibilities and achievements that align with information security, using action verbs to convey impact.
- Projects and Accomplishments: Highlight specific security projects you have led or contributed to, including metrics or results that illustrate your effectiveness in improving security posture.
- Education: Include your educational background, particularly degrees related to computer science, information technology, or cybersecurity, along with any relevant coursework.
- Technical Skills: Showcase your proficiency in security tools, software, and technologies, such as firewalls, intrusion detection systems, and encryption methods.
- Professional Affiliations: Mention any memberships in professional organizations (e.g., ISACA, (ISC)²) that demonstrate your engagement in the information security community.
- Tailoring Your CV: Customize your CV for each application by incorporating keywords from the job description, ensuring it resonates with hiring managers.
- Use CV Templates: Consider utilizing professional cv templates to enhance the visual appeal of your CV and make it stand out.
- Finalize with a Cover Letter: Complement your CV with a well-structured cover letter using our cover letter templates to effectively communicate your motivation and fit for the role.
- Utilize a CV Builder: Take advantage of a cv builder to streamline the CV creation process and ensure a polished final product.
Build your CV in minutes
Use an AI-powered cv builder and have your cv done in 5 minutes. Just select your template and our software will guide you through the process.